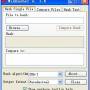
... the integrity of files by providing a hash algorithm you can use to check for any errors. ... WinHasher is that it supports a variety of hashing algorithms, including MD5, SHA-1, SHA-256, and many more. This means that you can choose the algorithm that best meets your needs, and verify the ...
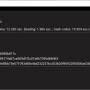
... minds at Geeks3D, is a powerful and versatile hashing tool designed for both casual users and professionals. ... efficiently. With support for a wide range of hashing algorithms, including MD5, SHA-1, SHA-256, and more, H4shG3n caters ... security needs, from data integrity verification to password hashing. One of the standout features of H4shG3n is its ...
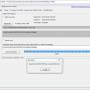
Looking for a tool that can quickly and easily verify the integrity of files? Look no further than Quick Hash, developed by software guru Ted Smith. With Quick Hash, you'll be able to generate and verify checksums with ease, so you ...

... MD5 Hash Generator" by Appnimi - a powerful Windows application designed to generate MD5 hashes of any ... Generator is its speed. Thanks to its cutting-edge algorithms, you can generate hashes for large files quickly ... is incredibly secure. MD5 is a widely used hashing algorithm that ensures data integrity and security. It's ...
... This powerful tool supports a wide array of hashing algorithms, including MD5, SHA-1, SHA-256, and more, making it ideal for developers, security professionals, and ...
... with. HashTab supports a wide range of hash algorithms including MD5, SHA1, SHA256, and many others. It also integrates seamlessly with Windows Explorer, making it incredibly easy to use. Whether you're an IT professional, developer, or ...
... encrypts your sensitive data with the strong SHA256 hashing algorithm, providing unmatched security against data breaches and cyber attacks. Designed with simplicity in mind, the ...
... comes to security. It uses the industry-standard SHA1 hashing algorithm to ensure that your files are protected against unauthorized access or modification. Whether you're ...
... SecurityXploded. This robust software offers a powerful encryption algorithm that can generate unique and secure hash codes ... in a matter of seconds. With its specialized algorithms, it provides ultimate encryption to protect against unauthorized ... sensitive data. The software is compatible with all Windows operating systems, and there is a free version ...

... can easily encrypt and decrypt files using advanced hashing algorithms, ensuring maximum security and privacy for their sensitive ... speed, EasyHash also offers a wide range of hashing algorithms to choose from, giving users the flexibility to ...