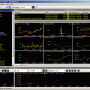
... model based on the data set by using proprietary algorithms. With the ability to handle large datasets, Adaptive Modeler saves time and eliminates the ...
... just a few clicks. Plus, BitCrypter's high-quality encryption algorithms ensure that your files are completely secure and safe from prying eyes. If you're looking for a reliable and user-friendly encryption tool, BitCrypter is an excellent choice. With its powerful features and ...
... are not tech-savvy. It employs advanced data recovery algorithms, which allow it to quickly retrieve lost files, even if they were damaged or deleted long ago. Not only is this software easy to use, it's also incredibly efficient. Magic Word Recovery ...
... your recovery needs. With its intuitive interface and powerful algorithms, Data Doctor Recovery Digital Camera makes the process ... formatted memory cards, and even inaccessible files. Its proprietary scan engine ensures that all possible data recovery scenarios are explored, maximizing the chances ...

... where to invest your money. The software’s advanced algorithms and analysis tools ensure that you stay ahead of the game, delivering accurate performance forecasts and cost-effective investment solutions. Additionally, IsoBourse boasts excellent customer support, readily available to provide expert assistance ...
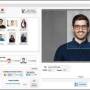
... their image editing workflow. With its advanced AI algorithms, Face Crop Jet ensures precision and accuracy, allowing users to focus on the creative aspects of their projects rather than tedious manual cropping. The user-friendly interface is perfect for both beginners and ...
... of your applications but also ensures that your proprietary algorithms remain confidential. Whether you're a developer looking to distribute your Excel solutions or a ...
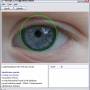
... recognition capabilities to their applications. With its advanced algorithms and convenient APIs, this software is suitable for a wide range of industries such as security, retail, and healthcare. Using the VeriEye Standard SDK Trial, developers can easily incorporate facial recognition features ...
... You can choose from a variety of encryption algorithms, including AES, Blowfish, Twofish, CAST, and more, ensuring the highest level of security for your files. You can also create hidden containers within your encrypted drive, which are completely invisible to ...
... its comprehensive search capabilities. With its deep scan algorithms, this software is able to find and restore image files in a wide range of formats, including JPEG, PNG, and RAW. It is even able to detect and recover fragmented files, ...