... a wide range of hashing algorithms, including MD5, SHA-1, SHA-256, and many more. In addition to its powerful hashing capabilities, VSFileHash also allows users to ...
Looking for a reliable and intuitive checksum tool? Look no further than Checksum Aide from Red Regent Software. This top-rated software quickly and easily generates and verifies checksums for files of any size, making it a must-have tool for both personal ...
Top Download Club is proud to present File Checksum Tool by KRyLack Software. This software is the perfect solution for those who worry about file integrity and security. File Checksum Tool verifies the authenticity of any file using a variety of ...
... of your downloaded files using the MD5 and SHA-1 hashing algorithms. With its user-friendly interface and quick processing speed, Free MD5 SHA1 Verifier is a must-have tool for anyone who wants to ensure the safety and security of their downloaded files. ...
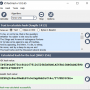
Top Download Club is thrilled to introduce VSTextHash developed by LOKIBIT.COM, a powerful and versatile software that has taken the tech world by storm. With VSTextHash, you can easily calculate the hash of any text, string, or file in the blink ...

... a variety of encryption algorithms such as MD5, SHA-1, SHA-256, SHA-384 and SHA-512. With Hash Codes, you can easily check the ... It's also compatible with multiple operating systems, including Windows, MacOS and Linux. Additionally, Hash Codes is completely ...

... a wide range of hash algorithms, including MD5, SHA-1, SHA-256, SHA-384, and SHA-512. What sets Hash Codes x64 apart is its user-friendly ...

Top Download Club is proud to introduce the revolutionary software, xCELLhash by FullScope Solutions. This powerful tool is a must-have for anyone in need of encryption and data protection. xCELLhash is capable of encrypting and securely storing large amounts of data, ...
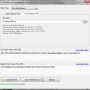
... security. This software supports hash algorithms such as SHA-256, SHA-1, and MD5, making it the go-to option for advanced level users. It utilizes open-source ...
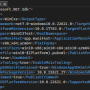
... a wide array of hashing algorithms, including MD5, SHA-1, SHA-256, and more, making it ideal for developers, security professionals, and anyone who needs to ...